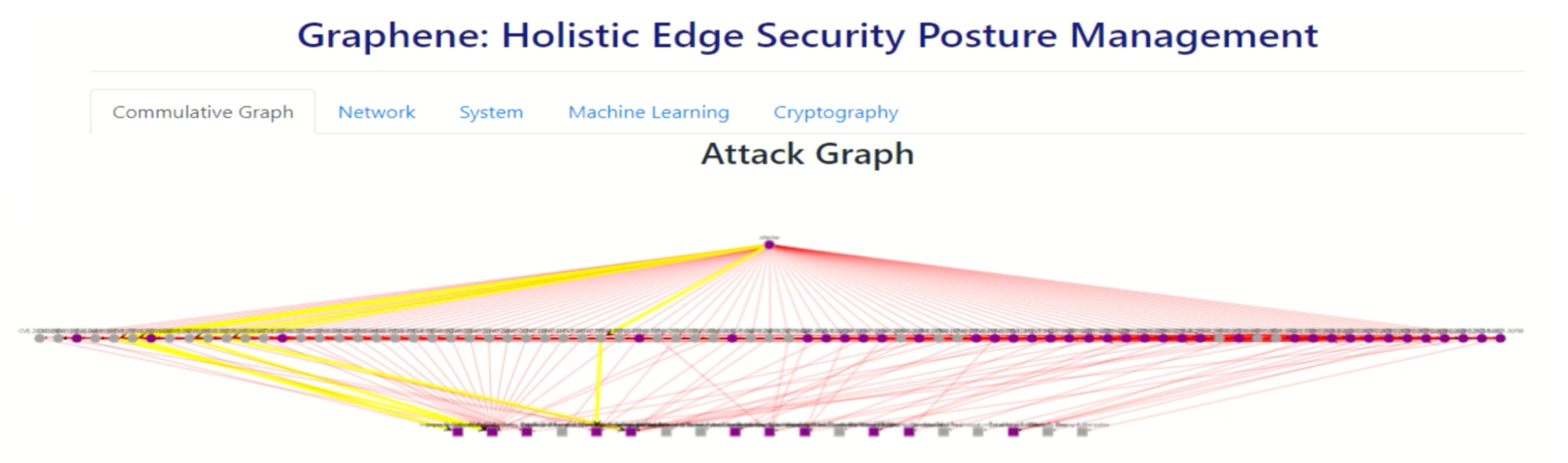
Graphene: Attack Graphs using AI
- Several questions arise in the mind of a CISO:
- How do you protect a distributed system and its crown jewels on cloud? What are the vulnerabilities and threats that exploit the weakest links? What are the weakest links? How does the attack surface look like and how it evolves over time? If the system has cloud, edge and IoT components, how would you address security of such a complex system?
- What are the crown jewels scattered across the network - a subset of data, models, system, applications, users and so on.
- What are the risks with respect to data flow, at-rest, in-motion, in-use and control-flow, user identities, as well as DevOps and ProdOps.
- It is time or long overdue to “Holistic security”
- Our solution develops a holistic 360-degree view of the evolving vulnerability and threat landscape focused a given system and its crown jewels, identifies weakest links, attack paths at that moment, and helps remediate and harden the system with more efficiency and less cost
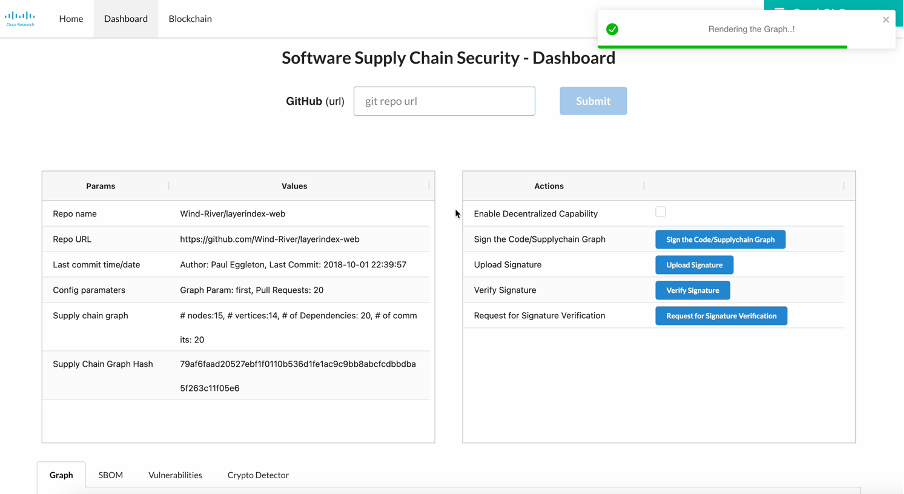
GraphBOM: Software Supply Chain Security
- What are the security risks due to the software supply chain, and how to remediate them?
- Is a given software and/or hardware system built or dependent on a vulnerable component during its build-time or runtime?
- What are the vulnerable components in the supply chain and how do they contribute to the risks and potential exploitation of the system in question?
- Who are accountable and how audit and compliance and remediation can be supported for the risks of the system and the associated components?
- Software supply chain security needs to be addressed
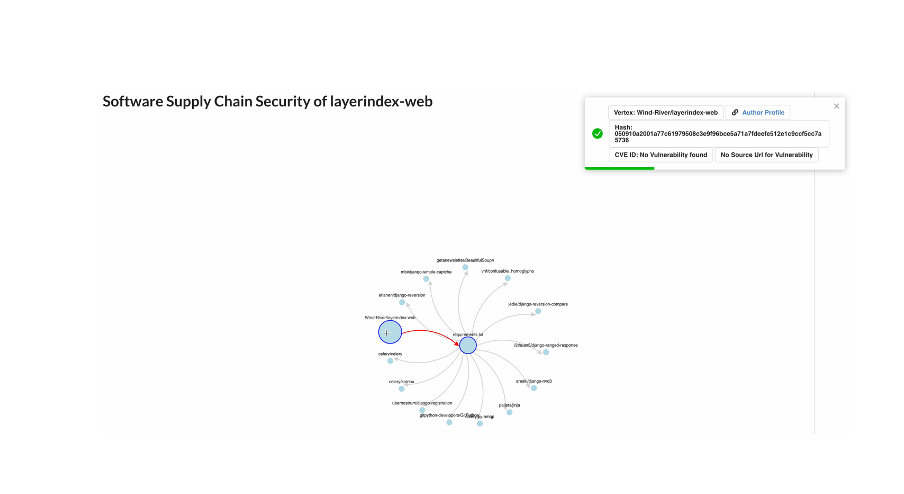
- as a supply chain graph instead of dependency tree
- as a de-centralized process as there are untrusted and semi-trusted parties contributing to the code.
- Our solution develops a decentralized software supply chain security platform using dependency graphs and graph-based cryptography that enables multi-party software dependency provenance, risk accountability and dynamic policy and license enforcement via smart contracts on software and hardware composition.