Quartz: Post-Quantum Security Risks & Remediation
Problem:
- Post-quantum cryptography risks within next few years
- network, data, cloud, APIs, software, hardware
- Cryptography libraries, configs scattered across the stack, across components/services, legacy
- Significant systemic challenges:
- Adoption of new cryptography protocols, libraries does not happen overnight
- NIST standard algorithms
Approach:
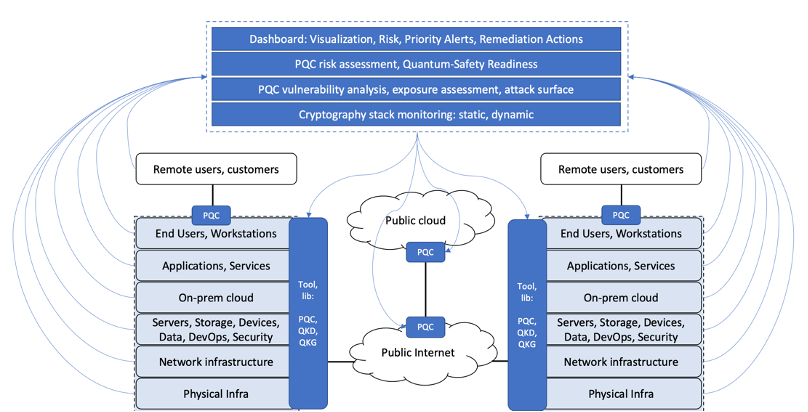
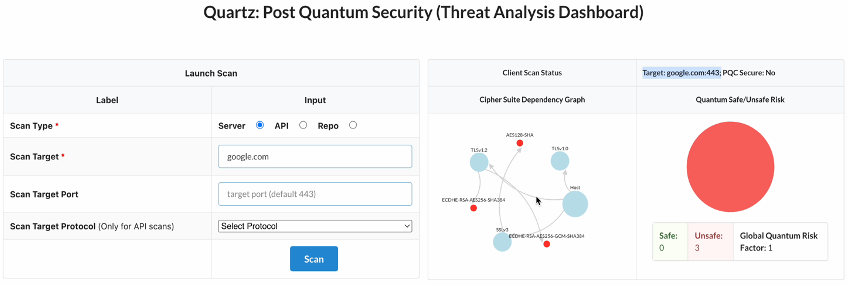
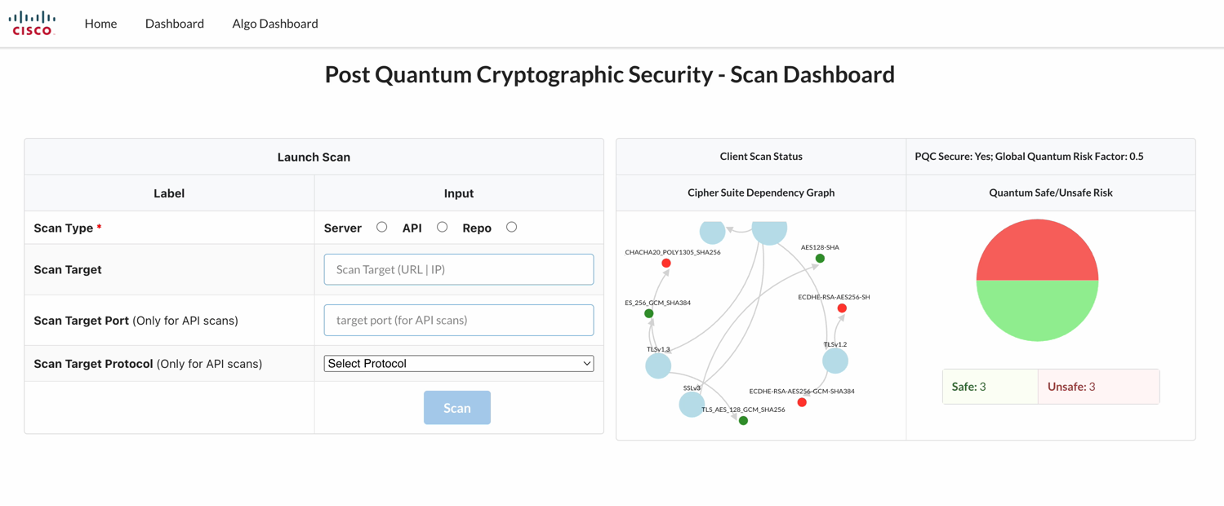
- Detect and monitor vulnerabilities, attack paths - ciphersuite dependency graph, cryptography BOM
- Measure: Automatically determine the attack surface, high-risk PQ-unsafe points
- Mitigate: Automatic PQ remediation planning
- PQ-safe algorithms, libraries, QKD/QRNG, …
- Carry out remediation
Quartz: Post-quantum security observability and posture analysis
- What are the vulnerabilities in a system with respect to quantum threats to cryptography?
- Is data flow - data-at-rest, data-in-motion, data-in-use quantum-safe?
- Is network and API connections are quantum-safe?
- Are hardware artefacts such as TPM, HSMs, secure enclaves quantum-safe?
- Are systems, decentralized blockchain platforms quantum-safe?
- Where are the quantum-specific vulnerabilities, risks in a distributed cloud system?
- Our solution carries out a quantum-specific threat analysis, risk analysis and remediation planning for such systems in a blackbox and whitebox manner.